Robotic Process Automation (RPA) has emerged as a transformative technology, revolutionizing, and reshaping the operational landscape of businesses across various industries. It has become a key driver of innovation and efficiency in today’s rapidly evolving business environment. In fact, according to the latest findings in a comprehensive report conducted by Grand View Research, the global market size for RPA was estimated to be a staggering $2.3 billion in 2022, demonstrating its significant market presence and immense potential for growth.
The future of robotics process automation services appears exceptionally promising, as it is projected to expand at an impressive compound annual growth rate (CAGR) of 39.9% from 2023 to 2030, according to the same report. While it is true that large enterprises dominated the RPA market share in 2022, accounting for a substantial 66.0%, the adoption and integration of RPA technologies are not limited solely to these industry giants.
On the contrary, small and medium-sized enterprises (SMEs) are anticipated to experience the highest compound annual growth rate during the forecast period. This is primarily due to the increasing awareness and recognition of the immense benefits and transformative power that RPA can offer within this segment.
The remarkable growth and vast potential of RPA solutions emphasize the importance for business and technology leaders to take proactive measures in future-proofing their RPA initiatives. However, it is equally crucial to address the challenges that arise during the implementation of this transformative technology.
Many stakeholders demand clear and direct benefits before approving technology investments, which can pose a significant hurdle for organizations. To unlock the full potential of RPA, it is crucial to understand that it is not a one-and-done solution. Rather, it requires a comprehensive approach involving planning, strategizing, and cultivating the right mindset to derive the maximum value.
In this context, Forrester has highlighted several critical steps, among which I firmly believe that the below three possess the potential to generate significant value and effectively futureproof RPA initiatives.
Integrate RPA seamlessly into your organization’s automation fabric
To effectively integrate RPA solutions into your company’s automation ecosystem, it is crucial to view RPA as an integral part of your overall automation strategy. RPA should no longer be seen as an isolated entity but rather as a steppingstone towards creating a comprehensive automation fabric. In fact, it should be considered a constituent of the broader automation roadmap.
In order to effectively align RPA solutions within your organizational structure, establish a dedicated automation organizational framework that focuses on transformation. This structure should have clear leadership and a well-defined charter that emphasizes the strategic objectives, operational goals, and governance of RPA solutions within the broader context of automation. While RPA is well-suited for automating repetitive manual tasks, its potential extends beyond mere cost avoidance. Explore transformation-centric use cases where RPA can act as a vital link in enabling digital business initiatives. By leveraging RPA as an enabler of digital transformation, you can unlock new avenues for innovation and drive business growth.
To ensure the success of your RPA program, it is essential to secure sponsorship from the C-suite. An executive sponsor plays a pivotal role in providing strategic direction, securing funding, aligning stakeholders, championing the program, and overcoming any obstacles that may hinder its progress.
Establish a robust business value model for RPA solutions
Calculating the return on investment (ROI) for complex processes becomes increasingly challenging due to various factors and dependencies. To ensure a realistic and comprehensive business case, it is essential to neither overstate the potential value nor underestimate the costs involved.
While the price of RPA licenses can vary significantly, the success or failure of achieving sustained ROI is independent of the license cost. To demonstrate the financial viability of implemented RPA solutions, take a balanced scorecard approach to assess the value generated by large-scale RPA programs that includes operational efficiency, business performance, revenue, profitability, customer experience and risk.
Understand the different cost structures involved, including infrastructure setup, licenses, automation development and testing, long-term running costs and the cost of change. Report automation value in ways that resonate with business leadership, focusing on functional, economic, experiential, and symbolic dimensions rather than solely tactical or productivity-focused metrics. Additionally, recognize the strategic and human impact of RPA within a broader automation initiative, acknowledging its ability to free up human labor for more innovative, consumer-centric, or socially impactful endeavors.
Approach RPA like an enterprise platform
When implementing RPA, it is crucial to treat it as an enterprise platform and adhere to the same standards and guidelines as other technologies. To ensure good automation governance, prioritize user experience, and involve business stakeholders and process experts in the design process.
Design the automation process responsibly by considering how they interact and impact actual users within the workflow. Apply user-centered design principles and involve experts to achieve user goals effectively. Formalize approaches to data privacy and resilience, as RPA bots handle sensitive customer and personal data. Also, be aware of vulnerabilities that may affect data provisions, such as compliance with regulations like GDPR.
To establish an effective automation architecture, focus on building platforms and supporting reusability. Develop a library of reusable components, business objects, or code that can be easily composed into various workflows, avoiding the need to rebuild from scratch. Maintain software development and testing best practices to ensure reliable and robust RPA solutions. While RPA simplifies automation creation for business users, it still relies on scripting across different workflows and applications. Complex tasks with extensive scripting can lead to bot failures due to infrastructure issues, software reliability and changes in application UI and data.
By embracing RPA as a vital component of your automation strategy, establishing a robust business value model and approaching it with the mindset of an enterprise platform, you can unlock the full potential of RPA and drive transformational outcomes for your organization.
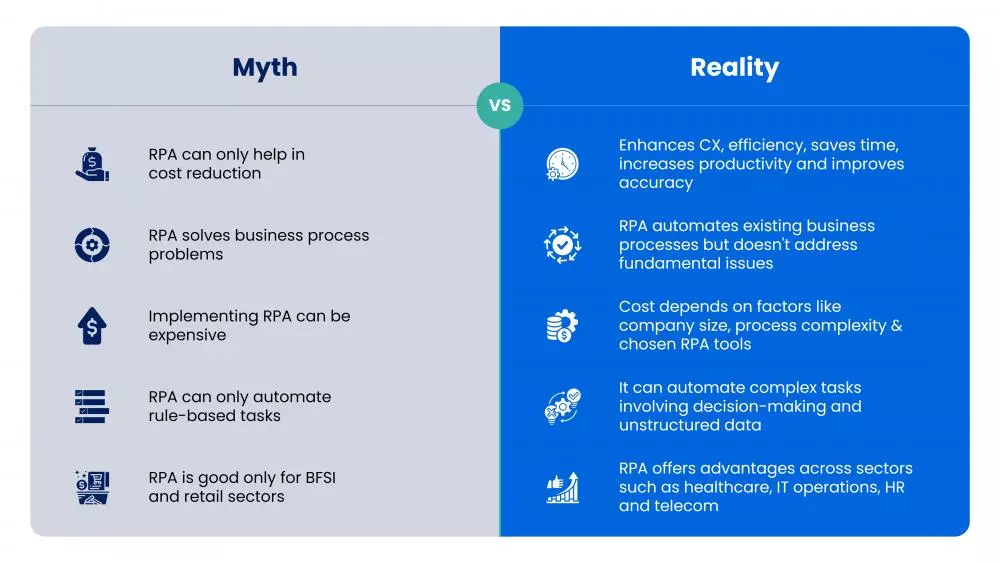
RPA: myths vs reality
As the demand for RPA continues to grow and organizations recognize its potential, it becomes very crucial to address the concerns and misconceptions that have hindered its widespread adoption.
Despite the evident success stories and statistical evidence supporting the value of RPA solutions, it has faced resistance from some industries when it comes to its adoption. Concerns have been raised regarding potential issues like overreliance on automated bots, susceptibility to cyber-attacks and the critical aspect of data security. These concerns have contributed to the creation of several misconceptions and myths surrounding RPA solutions.
Unfortunately, these misconceptions and myths act as barriers that hinder the widespread adoption and prevent businesses from fully harnessing the true potential of RPA solutions. Deloitte’s global robotics process automation survey report revealed a relatively small increase in organizations investigating or implementing RPA solutions and only 3% of leaders scaled their RPA capabilities to more than 50 robots.
In the below infographic, we debunk some of the most common myths associated with RPA.
Conclusion:
Robotic process automation is a powerful technology that can drive business transformation by automating repetitive tasks, improving efficiency, reducing costs, and enhancing the overall customer experience. By dispelling common myths surrounding RPA, organizations can gain a better understanding of its capabilities and make informed decisions about its implementation. Embracing RPA and leveraging its potential can accelerate digital transformation and help businesses stay competitive in the ever-evolving landscape of automation. RPA is not a one-size-fits-all solution and organizations must carefully assess their processes and objectives to determine how RPA can best be utilized to drive value and achieve their strategic goals.
We understand that RPA solution implementation is a specialized expertise and if not done accurately, it can cost a lot to any business. You may keep adding bots to your processes but not get desired results if you don’t know what to automate and how to improve existing processes while automating them. To help you navigate the intricacies of RPA implementation and maximize its potential, we have prepared a comprehensive whitepaper.

Our whitepaper offers a comprehensive perspective that highlights the lesser-known aspects of this technology. It also provides in-depth insights, practical tips and real-world examples to equip business and technology leaders with the knowledge needed to make informed decisions and execute successful RPA initiatives. Click here to access our whitepaper.