With the global cost of a data breach skyrocketing to an average of US$4.35 million in 2022, businesses are turning to technology advancements to safeguard their information and unlock new commercial opportunities. And, as companies ramp up their security efforts, a myriad of cutting-edge services and standards are emerging to help them stay ahead of the curve. Insurers are taking notice – and so should businesses!
To proactively tackle security threats, businesses often conduct vulnerability analysis of their internal networks or perform penetration tests on live websites, which can uncover security flaws with ease. But these measures alone are not enough. Data proves that businesses continue to fall victim to cyber-attacks, leaving sensitive data of customers, workers, or business partners vulnerable to theft or sale to competitors.
Enter Red Teaming- a comprehensive approach to security that not only combats vulnerabilities but also creates robust fences. In this blog, we will explore the power of red teaming and learn how it goes beyond technical aspects by additionally taking into account human factors such as social engineering, physical security, and other parameters that attackers may use to gain access.
Not reactive, but proactive
The evolution of red teaming as a security technique can be traced back to the military, where it was used to simulate attacks and test defenses during training exercises. Over time, businesses and government agencies began to adopt this approach to assess their own security posture and identify weaknesses in their defenses, before real attacks occur. Red teaming pretty much adopts the same premise as ethical hacking. The objective is two-fold: firstly, to assess the preparedness levels and secondly, to identify real-time gaps.
One specific business need that red teaming addresses is the need to be proactive in the face of an ever-evolving threat landscape. Traditional security measures such as vulnerability scanning and penetration testing are reactive in nature, meaning they are designed to detect and respond to existing threats. Red teaming, on the other hand, takes a proactive approach that simulates attacks from multiple angles, allowing organizations to identify gaps in their defenses and strengthen them before an actual attack occurs.
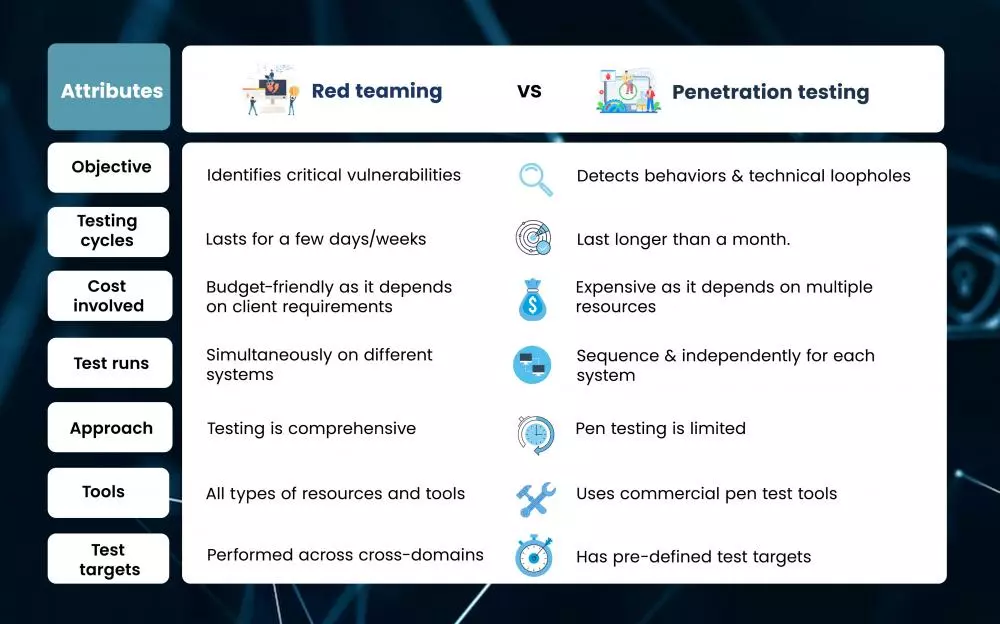
Red teaming Vs Penetration testing
Although red teaming and penetration testing share the objective of detecting and addressing vulnerabilities, their approaches differ in achieving robust security and creating a safer business environment. Red teaming is a comprehensive and methodical approach that involves a full scope cyberattack simulation to identify vulnerabilities and prevent attacks in any environment. In contrast, while penetration testing is essential, it is only a small part of what a red team exercise accomplishes. Penetration testers typically aim to gain access to a network, whereas red team operations have more ambitious goals.
Red team exercises evaluate defensive tactics and produce thorough risk analysis to simulate a more realistic advanced persistent threat (APT) scenario. Red teaming is a larger concept than penetration testing. Red teaming includes evasion and persistence, privilege escalation, and exfiltration, whereas penetration testing just simulates the first step in the cyber kill chain.
As Cybersecurity Ventures predicts, the global annual cost of cybercrime will reach $8 trillion USD in 2023. This and many more such data points drive home the message that cybersecurity experts must continuously innovate and develop more advanced solutions to combat cybercriminals and respond to emerging threats.
In the above context, implementing red teaming within an organization can provide numerous benefits, such as:
- Assessing the organization’s defense system through simulated cyberattacks to determine the security level of policies
- Categorizing related assets according to risk level
- Detecting and exposing security vulnerabilities and loopholes
- Evaluating the effectiveness of the organization’s security system during an attack
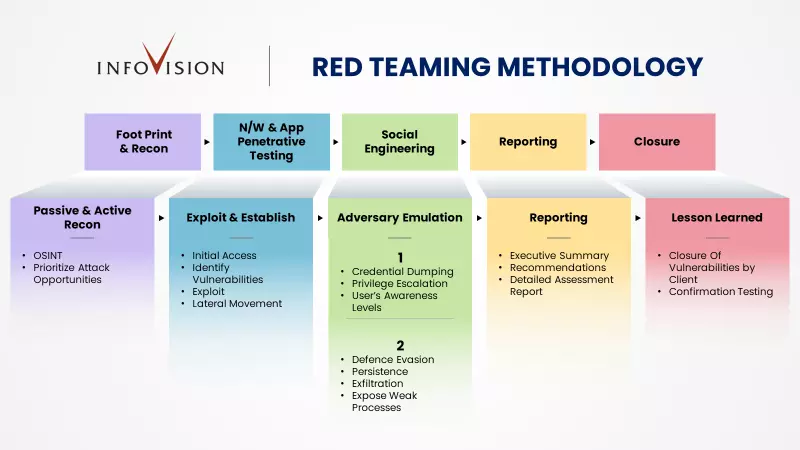
Typical red teaming approach
1. Foot printing & reconnaissance:
Foot printing & reconnaissance is one of the pre-attack phases, which refers to the actions taken before the attack itself. In other words, the examination of the security posture of the target organization’s IT infrastructure begins with foot printing. A hacker can gather the following data during this stage:
- Domain name
- IP Addresses
- Namespaces
- Employee information
- Phone numbers
- E-mails
- Job Information
2. Network penetration testing and application security testing:
Network penetration testing focuses on identifying vulnerabilities in an organization’s network infrastructure, including routers, switches, firewalls, and other network devices. It aims to simulate an attacker’s actions to gain unauthorized access to sensitive information or compromise the network.
Application security testing involves assessing the security of software applications, including web applications, mobile apps, and other custom-built software. The objective is to identify vulnerabilities that can be exploited to gain unauthorized access, manipulate data, or disrupt the application’s normal functioning.
3. Social Engineering:
Social engineering is a manipulation technique that exploits human error to gain private information, access, or valuables. In cybercrime, these “human hacking” scams tend to lure unsuspecting users into exposing data, spreading malware infections, or giving access to restricted systems. Attacks can happen online, in-person, and via other interactions.
Generally, social engineering attackers have two goals:
- Sabotage: Disrupting or corrupting data to cause harm or inconvenience.
- Theft: Obtaining valuables like information, access, or money.
4. Reporting and analysis:
After the red team’s simulated attack is complete, you’ll go through a reporting and analysis process to determine the path forward. You’ll see how your blue (defensive security) team performed and which key vulnerabilities need to be addressed.
The red team prepares a comprehensive report detailing their findings, including vulnerabilities exploited, attack paths, and recommendations for improving security. The report is typically shared with the organization’s management and relevant stakeholders.
5. Closure:
Once the attack is over, the final closure stage begins. This stage does not only mean managing the leftover digital remnants of the executed attacks. It also means providing the Blue Team with one or more evaluation sessions where the complete timeline is replayed in a workshop to maximize learning and awareness. The result of this phase is a detailed technical report and a perspective on your overall security maturity in your threat landscape.
Why strategize red teaming for your business?
Investing millions of dollars to protect your network may make it seem unwise to employ a team of bug hunters to intentionally breach it. However, as enumerated above in the article the ever-evolving threat landscape makes it imperative to have adequate guards in place.
To learn more about an effective red team strategy that can ensure optimal security for your organization, contact the InfoVision Red Team at info.ecrs@infovision.com.